VirusTotal Monitor Partner's aim is to ease false positive handling by antivirus companies. It is designed to provide VirusTotal participating AV scanners with hashes, file content, metadata and ownership information for any detection of a file in a Monitor collection. Note that files will only be shared upon a false positive.
As stated in VirusTotal Monitor overview software developers having an account in Monitor can upload their goodware collection to be periodically analysed by participating antivirus scanners. Note that these accounts are handed over to users once VirusTotal staff verifies and identifies them. Any of the hashes detected by your engine will be available in the Monitor Partner webapp or via the API calls documented bellow.
A common flow is described below:
- A Monitor account is handed over to a user.
- Users upload some files and make some comments on them in the details metadata section.
- At some point in time or just after being uploaded a file is detected by your engine.
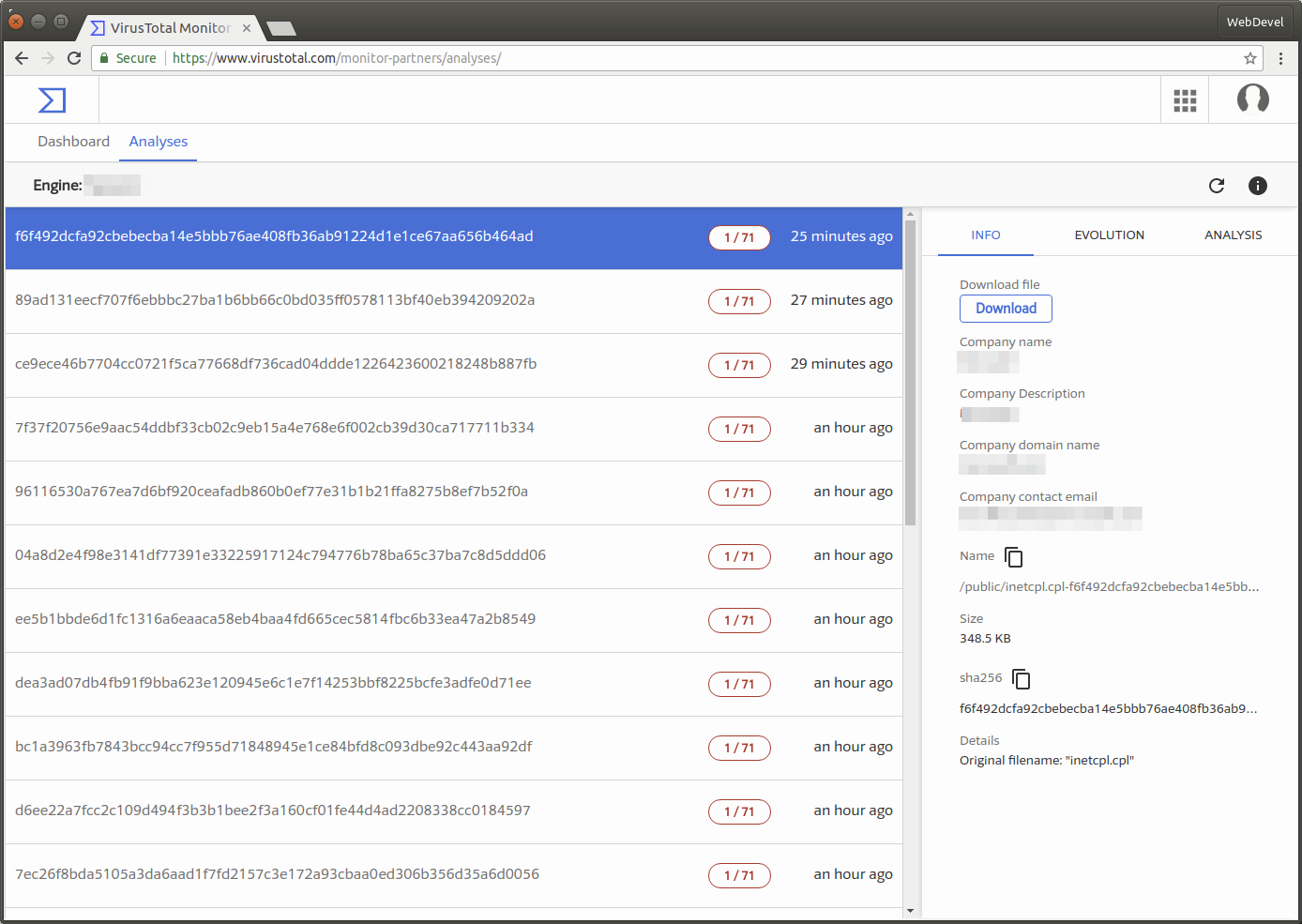
- A new hash appears in the /hashes endpoint or in the website Analyses tab.
- You request items to get files with that particular hash from any user collection, a hash could appear in different collections with different details. This situation (one hash/many files) may happen for example because sometimes software developers include certain versions of operating system files with their binaries, so one owner may be the operating system developer and the rest some other software developers. The details about each item owner can be obtained requesting the Monitor API endpoint.
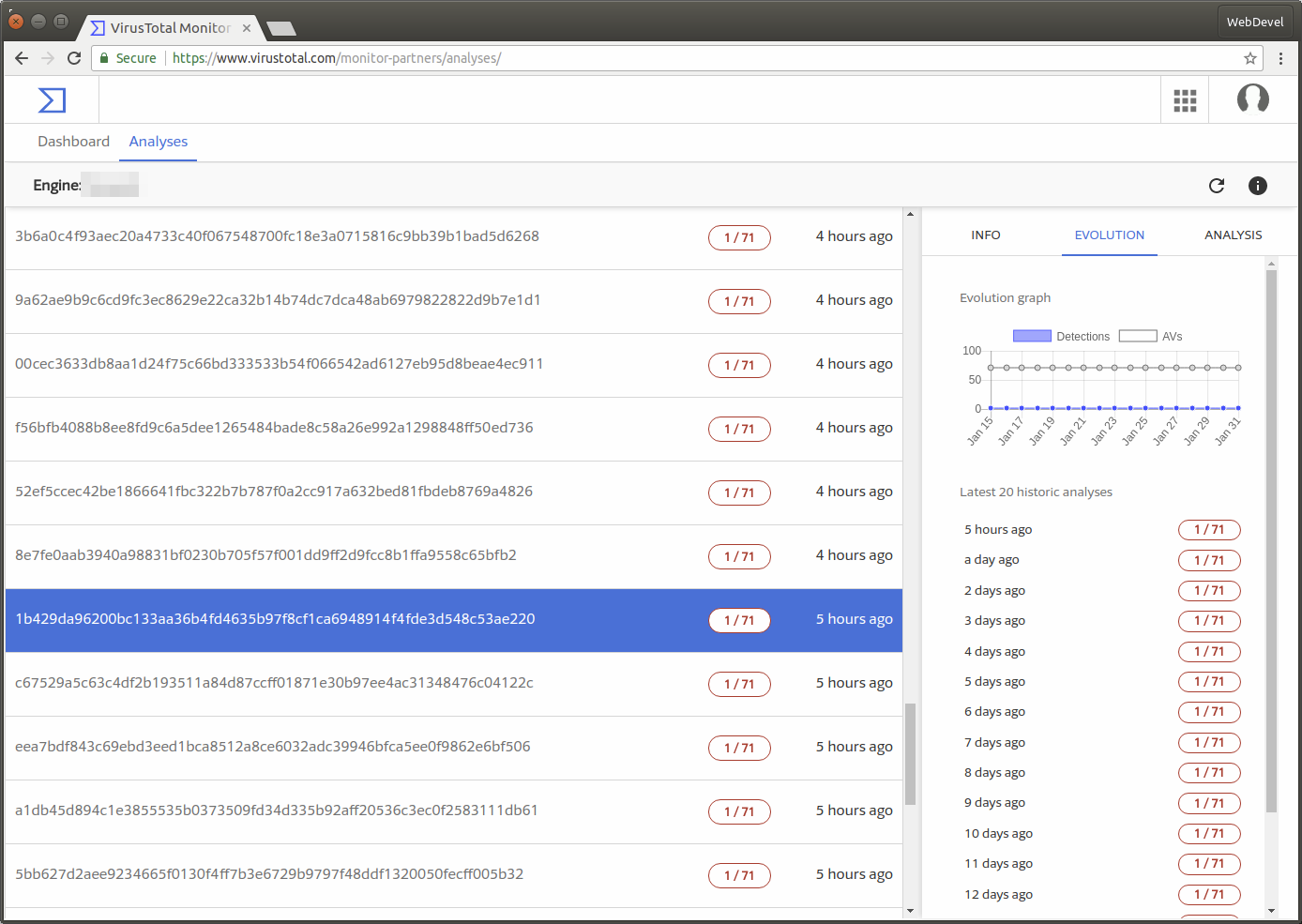
- You can also request hash analyses to get hash historic scanning information.
- Once a false positive is confirmed your engine signatures may be updated and in the next cycle and the hash will disappear from the Analyses.
- Alternatively, you can confirm that the detection is correct and hide it from your analyses posting
a comment over it. You can always access these hashes filtering with ignored tag over hashes and revert this action.
For your convenience we generate a daily CSV formatted file with company name, hash and url with your detections. A new bundle is available each day at 1am UTC.
Additionally you can use this example python script to generate a similar report for your account at the current time, it will download all related hash files and its metadata storing it on your filesystem in json format.
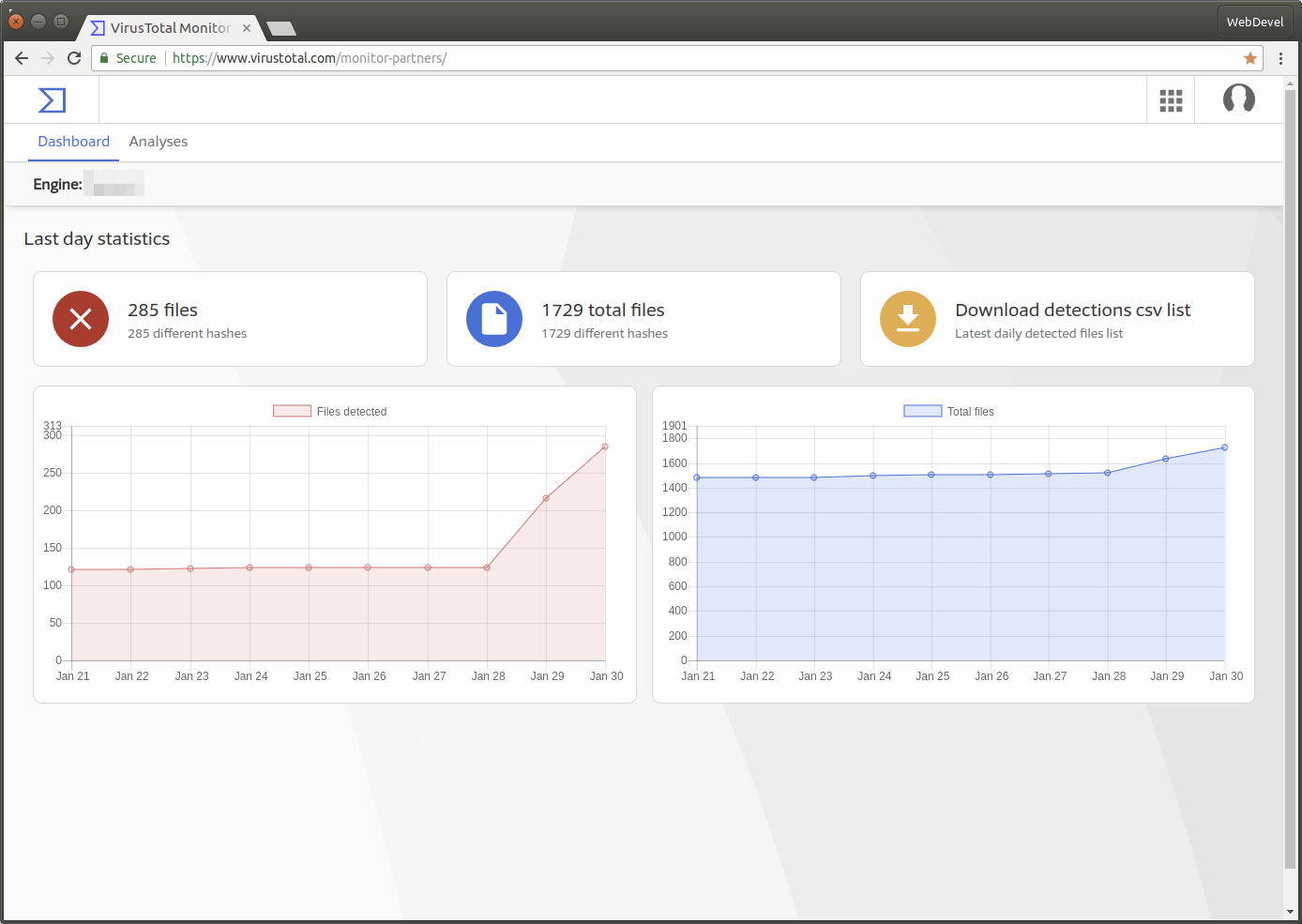
You can also access information about your engine detections and collection size in daily statistics.
Here are some Monitor Partner website captures: